Disaster Preparedness Toolkit
This toolkit includes four webinar recordings, a comprehensive resource guide, model ordinances and agreements, and supporting materials for cities.
The ‘10X downtowns’ route to better city centers
As cities adapt to the demands of the 21st Century, the vitality of their downtowns has never been more critical.

Housing
Article
Inside Sandy Springs’ Housing Challenge: Navigating Market Forces
September 10, 2025
In this Q&A, Sandy Springs Mayor Rusty Paul discusses how redevelopment, zoning reforms, and the realities of market forces are shaping the city’s housing challenge.
Housing
Resource Link
Georgia Deam Program
Georgia Department of Community Affairs (DCA) is the State of Georgia's Housing Agency. DCA provides opportunities for Georgia's citizens to obtain safe, decent, affordable housing through a range of programs designed to foster new housing development, finance homeownership and encourage improved housing choices.

Information Technology & Cybersecurity | Parks & Recreation
Resource Link
To connect residents with nature, one Georgia town is turning to tech
In one Georgia town, officials are leveraging tech and data to bring people closer to nature.

Children & Youth | Workforce Development
Article
Jump Starting Economic Mobility: How Savannah Is Investing in its Youth Workforce
August 28, 2025
Savannah is tackling poverty and childcare shortages through its EMERGE program and Jump Start initiative, offering free credentials, training, and support to boost youth mobility and expand the childcare workforce.
Finance
Resource Link
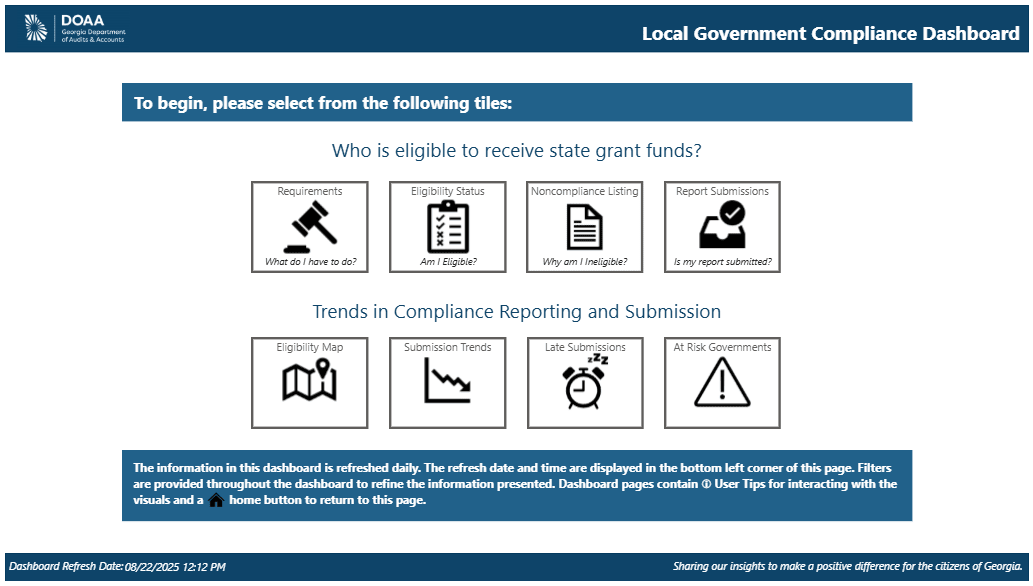
Local Government Compliance Dashboard
State law requires local governments to submit financial audit reports to DOAA and requires DOAA to report on compliance with this requirement. This dashboard enhances public access to current information on local government financial reporting.
